Malicious Browser Extensions
As we do more and more of our day-to-day tasks online, our web browsers have become an irreplaceable tool for many people. Often, we decide to augment the default behavior of these browsers with browser extensions to provide custom functionality to our browsers in order to make the tasks that we perform online easier. However, with the introduction of browser extensions comes a large attack vector that could be used to serve us advertisements, circumvent web security features, or even gain access to our computer. In the case of mobile apps, relying on the official "store" significantly reduces the risk of installing malicious software. Unfortunately, in the case of browser extensions, the official web stores are not nearly as efficient in recognizing malicious extensions, with there being several cases of malicious browser extensions making it onto the Google Chrome Web Store and being ranked ahead of the legitimate extensions in search results:
http://www.pcworld.com/article/3027642/security/googles-chrome-web-store-lists-malicious-chrome-apps-ahead-of-legit-extensions.html
Since CyberPoint is in the business of protecting what is invaluable to you, I hope to provide some guidance as how to better avoid malicious extensions.
The Danger of Extensions
Browser extensions have a surprising amount of power and control over a browser and the content that is displayed. An extension can inject scripts into rendered pages, create, redirect, or block web requests, or steal information that is entered into online forms. An analysis of browser extensions by researchers at the University of California found that out of ~48,000 browser extensions that they evaluated, the 130 extensions were clearly malicious and over 4,700 additional extensions exhibited suspicious behavior. This is clearly alarming as 10% of the extensions that they evaluated were malicious or suspicious. What is perhaps more alarming even still is the ease of which malicious behavior can be added to a browser extension. In order to evaluate the ease of which malicious behavior could be added to an extension and to learn how to better defend against a malicious extension, I decided to develop a "malicious" Google Chrome browser extension. The result was surprisingly easy for someone without any prior extension development experience.
Busting Frame Busting
Clickjacking is an attack which conceals hidden links underneath legitimate links so that when a user attempts to click on a legitimate link the user is redirected to a malicious link. Frame busting is a technique that is commonly used to prevent clickjacking attacks thus allowing an attacker to direct an unknowing user to an exploit server or an advertiser that would then pay the attacker for the "advertisement." Frame busting works by detecting the hidden frames that are used in clickjacking attacks and then removing those frames from the webpage. In 2010, researchers at Stanford presented a paper on the flaws in commonly used techniques to prevent clickjacking attacks through the use of frame busting (https://www.usenix.org/system/files/conference/usenixsecurity14/sec14-paper-kapravelos.pdf). After reading this, I set out to develop a browser extension to "bust" commonly used frame busting techniques through a generic attack that would be delivered through my browser extension and could enable an attacker to hijack a user's web session.
It became almost immediately clear how simple this would be. After reading the paper it became clear that if I could get control of the content of a web page that I could bypass frame busting with a simple javascript command:
self = top;Yes, that is it. If given control of a web page, a one-line script can bypass the vast majority (~80% according to the Stanford study) of frame busting techniques, enabling further attacks. Now the question is, "how easy is it for a browser extension to inject scripts into a webpage?" I had (incorrectly) assumed that injecting scripts into a web page would require jumping through some hoops in order to get access to all of a user's web content. Here is what permissions are required to inject my script into all web pages:
"permissions": ["http://*/*", "https://*/*"]And just like that, I now have the required accesses to bypass most commonly used frame busting techniques through injecting code into webpages. Using the provided APIs for Chrome Extension development made injection of the script into the web page itself to be trivial. In fact, the entire process of developing an extension that bypassed most frame busting mitigations took around 30 minutes from start to finish.
Avoiding Malicious Browser Extensions
The ease of which browser extensions may be developed has allowed a large amount of very useful extensions. Unfortunately, that ease of development has also allowed many malicious extensions to have been developed and to be released into the official browser extension marketplaces. Additionally, safe extensions often require the same permissions that are requested by malicious extensions. For example, at the time of my writing this, the "Grammarly" extension was the most popular extension in the Chrome store. This extension is offered by a trusted company, has over 10 million users, and is by all accounts a "safe" extension. Below is a screenshot of the permissions requested by that plugin:
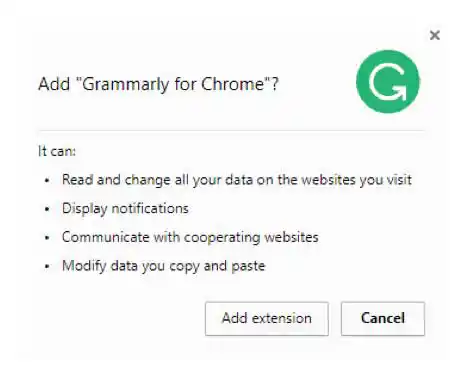
The first permission listed there is the same permissions that are required by the "malicious" plugin that I wrote. Since the permissions do not provide any insight into how the extension is using the permissions that we give it (is it correcting my grammar or is it injecting scripts to bypass security features), this leaves the question, "How do I avoid malicious extensions?"
As is the case for many aspects of cybersecurity, the best defense against rogue browser extensions is an educated and careful user. The next time you're installing a browser extension, following the procedures below will help you protect what's invaluable to you.
- Use the official store. Although this doesn't guarantee your protection, an extension that is not offered through the official store raises an immediate red flag.
- Verify the publisher of the extension. If you are installing an extension that claims to be developed by a major company, ensure that you don't install a similarly named extension by a malicious author.
- Check the reviews and number of users. Malicious authors may try to use bots to give the extension positive ratings. Manually check to see the number of users and read reviews to see if users report any suspicious behavior of the extension. A major company's extension should have a large number of users, if the extension has a small user base, that could be red flag that the extension is disguising as another extension in order to get more users.