Old Exploits Up to Old and New Tricks: TrickBot
The classics never get old, do they? Sometimes an old classic receives a new look, like the remake of West Side Story or Ghostbusters. In the case of Conti ransomware, the classics that never get old are TrickBot and Cobalt Strike, used by Conti to distribute their ransomware. In the case of TrickBot, the remake comes with creative new obfuscation techniques. This article discusses the current incarnation of TrickBot, its historical evolution, new tradecraft it employs, and what the future holds according to some hints dropped in recent weeks.
TrickBot certainly merits the discussion, as the stakes involved are high. During its campaigns, TrickBot has been used for bank account takeover, high-value wire fraud, and ransomware attacks striking critical organizations, to name a few of the consequences of its deployment.

History
Through the Server Takedown
As stated by every article that has ever been written about Trickbot, TrickBot began life as a banking trojan intended to steal banking credential. It did not remain in that bucolic state for long. Over the years, the TrickBot threat actors, the organization that developed and distributed TrickBot, turned it into a coherent, modular malware system and, until the fall of 2020, built TrickBot into a botnet with an estimated one million bots in its control. The botnet proved valuable as an entry-point for other threat actors' malware campaigns, so the TrickBot threat actors turned their system into malware-as-a-service. Most notably, the service was used by the cyber criminals behind the Ryuk ransomware.
An orchestrated response by legitimate service providers around the world shut down the TrickBot network's Command and Control (C2) servers in October, 2020. Microsoft, which participated in the action, has a very complete discussion of the takedown and the inner workings of a TrickBot campaign at that time.
After the Takedown: Involvement with Conti Ransomware
The developers behind the malware were not prepared to go gently into that dark net; TrickBot rose again after the takedown, adapted, and became an integral piece of the current Conti ransomware campaign. The Conti ransomware campaign has been a severe one, with the Cybersecurity & Infrastructure Security Agency (CISA) issuing an alert in September 2021 (reissued March 9, 2022).
The marriage of TrickBot and Conti, however is not a software marriage, but appears to be more of a merger or acquisition. Following the worldwide destruction of the server network built by TrickBot, the top members of the TrickBot organization, perhaps tired of the years of attacks on the TrickBot system, went to work for the Conti ransomware group, including developers.
Delivery
The preferred methods of delivery vary widely, but depend largely on spam or phishing campaigns or via droppers. Spam depends largely on common baits, such as delivering fake invoices, greeting cards, and so forth.
The main initial infection method is malicious Office documents, such as Word or Excel documents. By tricking the victim into enabling macros, TrickBot is able to execute VBS and download the TrickBot binary.
Evolution & Adaptation
The history of this malware and its return following October 2020 show that, if nothing else, TrickBot's developers are committed to the project. With its return came new capabilities.
Recon
In February of 2021, researchers discovered a new reconnaissance module in TrickBot. TrickBot developers added the masscan port scanner to TrickBot's arsenal, foregoing its previous scanning tool (called LightBot). The mass port scanner (called masrv) has its own TCP/IP stack and can scan enormous portions of the Internet in minutes. The uses of the scanner are obvious: TrickBot maps victim networks and tracks any open ports it may find on a device, sending the information back to C2.
According to the Kronos Logic Vantage Team:
"The module arrives as either a 32-bit or 64-bit DLL, depending on the Windows OS version of the victim machine the bot is running on. Both DLLs we observed are debug builds and log their execution into standard output.
"As with other TrickBot modules, the module is executed via its export functionsStartandControl."
Open port information sent back to C2 is reviewed to determine the device's value as a target for exploitation.
The following list of HTTP Commands is from the Kronos Logic Vantage Team's report on the masrv module:
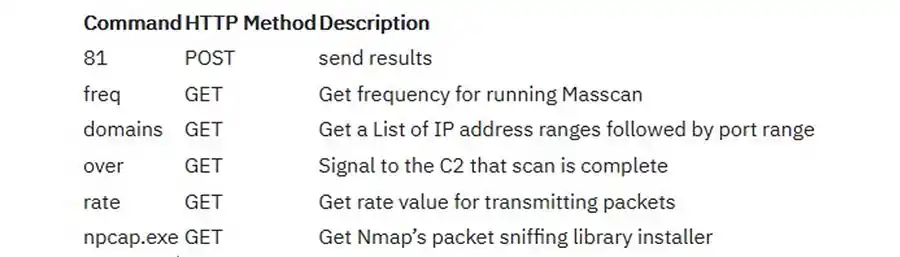
Module C2 requests (Kryptos Logic Vantage Team)
Perhaps the most valuable content in the Kronos Logic Vantage Team's report are Indicators of Compromise (IoC) and YARA rules for the masrv module.
Evasion and Obfuscation Techniques
TrickBot employs a variety of defensive techniques to evade detection and obfuscate its contents from analysis, as described in the IBM Trusteer.
TrickBot's first line of defense are server-side injections, avoiding loading into infected machines and alerting administrators. This means injections are less likely to be seen by security researchers and also means the injections can be more easily maneuvered.
Additional evasive tradecraft employed by TrickBot is using HTTPS to retrieve injections from its C2 server. The module sets flags that determine the victim's browser page, lock data streams, decide when to ignore requests it doesn't like, prevent assessment of communication flows, and block showing certificate errors.
Another method employed is to anticipate the actions of a security researcher and cause the page under analysis to crash when the researcher employs a common method used in deobfuscation. In this instance, when the researcher tries to employ Code Beautification, a memory overload crashes the page.
Going further, TrickBot injection code obfuscated. It is encoded with Base64 so that scripts are not viewed in plain text, then the following techniques are added:
- Minifictionb/uglification
- String extraction and replacement
- Number base and representing
- Dead code injection
- Monkey patching
IoC
In its reissued alert, CISA was provides Indicators of Compromise (IoC) for administrators to use in determining if their machines are compromised. The IoC are a list of domains with registration and naming characteristics similar to domains used by groups that have distributed Conti ransomware.
Additional Useful Resources
Also of note, the CISA alert contains:
- a description of the MITRE ATT&CK Techniques,
- recommended mitigations,
- and a Response Checklist in Case of Infection.
The Future of TrickBot
There is a report that TrickBot's final evolution mimics legitimate software by being retired in favor of a new application. TrickBot is scheduled for replacement by BazarBackdoor, new malware from the developers of TrickBot, which is designed as a malware access point into infected networks.
Contact SRT
CyberPoint's SRT Team support incident response with repository querying and analysis. We also respond to customer inquiries about a wide array of infosec topics.
If your organization needs immediate assistance with a suspected or confirmed cyber incident, contact us.