Software Defined Security at CyberPoint
Software-defined networking, commonly referred to as SDN, has received a lot of press recently regarding both the technology itself and the impact that it will have in the networking world. At CyberPoint, being a cybersecurity company, we got curious and decided to take a look at the impact that SDN could have on security.
Software-defined networking is a software abstraction of low-level network functionality. This software management of the network functionality takes place within an SDN controller. These SDN controllers commonly provide learning switch logic, basic firewall functionality, VLAN separation, and other general logic related to the traffic shaping and network control.
After looking into software-defined networking from a security standpoint, we quickly realized that this technology had the potential to be either a great asset, or a terrible weakness in a network's security. On one hand, having a centralized view of a network allows for more intelligent and complex network security policies to be implemented. However, this ability to control the network from a single point also introduces a large target to a network. Why would an adversary spend their time compromising individual hosts if they could simply compromise the controller and have access to the entire network?
At CyberPoint, we are in the business of protecting what's invaluable to you, so we also looked into ways to leverage this new software-defined networking technology to further enhance network security. In particular, we noticed that there was not a framework to implement security policies along with corresponding responses to violations of those policies. What we envisioned was a general framework to allow organizations to define custom security policies and responses in order to fit their needs. A framework such as this could allow network administrators to have responses in place to run automatically when a certain event occurred which could reduce or eliminate the damage that is typically done in the time between an attack occurring and when the network team is first able to respond.
With this idea, we started building Galatine, an open-source framework designed to fill the gap in security application caused by the lack of SDN security frameworks. This framework was built using the pyretic SDN controller programming language. Pyretic is a python module which forms and sends messages using OpenFlow, a standard protocol for communications between the control and forwarding layers of SDN architectures1>. While there are many popular SDN controller programming languages, OpenFlow is the protocol which nearly all of them use for communications as it is the most commonly supported SDN protocol by networking hardware vendors.
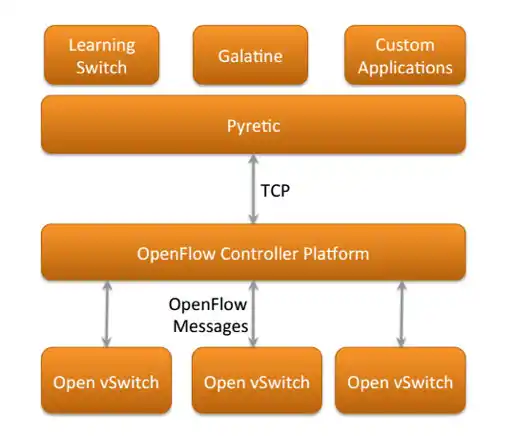
The Galatine framework was built for the purpose of being able to detect malicious hosts based upon their behavior as well as having the ability to detect the malicious traffic prior to the attack reaching its intended target.
Once we built the Galatine framework, we set about providing some basic examples of security applications this framework is capable of detecting in order to prove Galatine's effectiveness. A great example of the effectiveness of this type of security application is in the case of a malicious host performing ARP spoofing.
In this example, the policy that we have created in order to detect ARP spoofing (and provided as an example on github) detects when a machine claims to have some IP address when we have a different IP address associated with that machine. At that point, Galatine detects the unexpected behavior, but double checks to ensure that it does not perform a remediation against a non-malicious host. In order to double check the behavior of the host, Galatine sends out several ARP requests and checks to see if the suspicious host claims to be other IPs that are not associated with that host as well. If the suspicious host is not consistent with regards to the IP that it claims to have during the double check, then Galatine marks that host as performing ARP spoofing and performs the associated remediation.
While this is just a simple example of what can be accomplished with Galatine, it is easy to imagine the possibilities when a flexible technology such as SDN is applied to network security. Now network administrators can have automatic responses in place to respond to various types of events on their networks, significantly reducing the time needed in order to put a response in place.
It is our hope at CyberPoint that advancements in SDN technology will bring about more products like Galatine can help tilt the playing field in favor of organizations trying to protect their invaluable resources.
If you want to learn more about how SDN and technologies like Galatine can be used to protect what is invaluable to your organization, then contact CyberPoint. Our experts can evaluate your organization's security posture and determine the best method of using these state of the art technologies in order to protect your organization.